Hackers and Viruses 2
1)Who is the author of the book "The Art of Intrusion "?


2)Identify this hacker of Indian origin?
3) The famous Sprawl trilogy "Neuromancer (1984), Count Zero (1986), and Mona Lisa Overdrive" has been written by whom?
4) "X' is a hacking technique designed to conceal the compromise of a computer's security, and can represent any of common program. Identify X?
5)Identify him
6)His first hacking endeavor was to make free long-distance calls by creating “blue boxes” to bypass phone-switching mechanisms, and some of his college friends claimed that he had called the Pope, pretending to be Henry Kissinger. Identify him?
7)Connect



8)"X" is a term coined to describe the study, experiment and exploration of telecommunication systems, such as equipment and systems connected to public telephone networks.
What is the term?
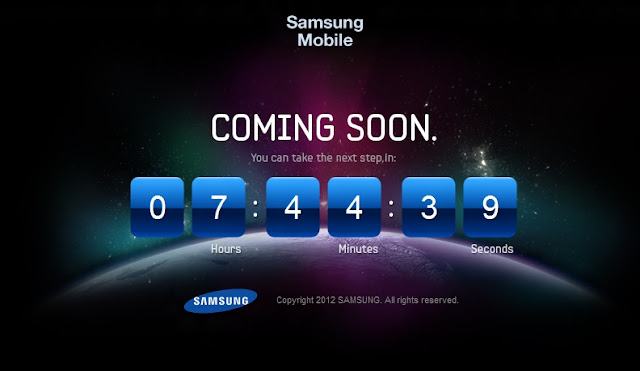
9)What is the significance of this pic?

10)It is a term understood to mean the art of manipulating people into performing actions or divulging confidential information.It is very frequently used for hacking purposes. What is the term?
7)Connect



8)"X" is a term coined to describe the study, experiment and exploration of telecommunication systems, such as equipment and systems connected to public telephone networks.
What is the term?
9)What is the significance of this pic?
10)It is a term understood to mean the art of manipulating people into performing actions or divulging confidential information.It is very frequently used for hacking purposes. What is the term?
Comments
Post a Comment